 Offline
Offline

Complete Free handbook of Network Management & Security with diagrams
The app is a complete free handbook of Network Management & Security which covers important topics, notes, materials & news on the course. Download the App as a reference material & digital book for Cloud Computing, security, computer science engineering, networking, software and communications, software engineering programs & degree courses.
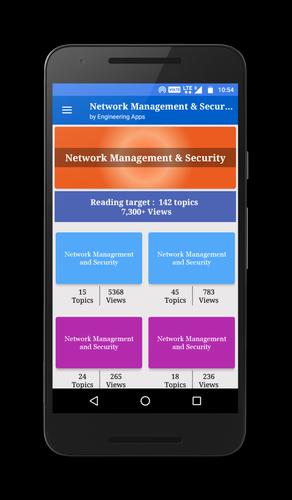
Network Management & Security useful App lists 140 topics with detailed notes, diagrams, equations, formulas & course material, the topics are listed in 5 chapters. The app is must have for all the engineering science students & professionals.
The app provides quick revision and reference to the important topics like a detailed flash card notes, it makes it easy & useful for the student or a professional to cover the course syllabus quickly just before an exams or job interviews.
Also get the hottest international engineering & technology news on your app powered by Google news feeds. We have customised it so that you get regular updates on subject from international/national colleges, universities, research, industry, applications, engineering, tech, articles & innovation.
Network Management & Security is the best application to remain updated on your fav. subject.
Use this useful engineering app as your education tool, utility, tutorial, book, a reference guide for syllabus and explore study course material, aptitude tests & project work.
Track your learning, set reminders, edit, add favourite topics, share the topics on social media.
Some of the topics Covered in this application are:
1. Introduction to Network security
2. Security attacks
3. Active and Passive attacks
4. Security Services
5. Security Mechanisms
6. A Model Of Inter-Network Security
7. Internet Standards
8. Internet Standards and RFC’S
9. Buffer Overflow
10. Format String Vulnerability
11. Session Hijacking
12. UDP Session Hijacking
13. Route Table Modification
14. Address resolution protocol attacks
15. Man-in-the-middle attack
16. Conventional Encryption principles
17. Cryptography
18. Cryptanalysis
19. Substitution Encryption Techniques
20. Playfair Ciphers
21. Hill Cipher
22. Polyalphabetic Ciphers
23. Pigpen Cipher
24. Transposition techniques
25. Feistel Cipher Structure
26. Feistel Cipher Decryption
27. Conventional Encryption Algorithms
28. S-DES key generation
29. S-DES Encryption
30. Data Encryption Standard
31. Single round of DES algorithm
32. Triple Data Encryption Standard
33. International Data Encryption Standard
34. Blowfish Algorithm
35. Blowfish Encryption Decryption
36. Advanced encryption standard
37. S-AES Encryption and Decryption
38. S-AES key expansion
39. The AES Cipher
40. Substitute Bytes Transformation
41. ShiftRows Transformation
42. MixColumns Transformation
43. AddRoundKey Transformation
44. AES Key Expansion
45. AES Decryption
46. Cipher Block modes of Operation
47. Cipher Block modes of Operation
48. Cipher Block Chaining Mode
49. Cipher Feed Back Mode
50. Output Feedback Mode
51. Counter Mode
52. Message authentication
53. Message Authentication Code
54. Message Authentication Code Based on DES
55. Hash function
56. MD5 Message Digest Algorithm
57. MD5 Compression Function
58. Secure Hash Algorithm
59. RIPEMD-160
60. HMAC
61. Public-key Cryptography
62. Attack on Public-key Cryptography
63. Applications for public-key cryptosystems
64. RSA algorithm
65. Fermat's and Euler's theorem
66. Security of RSA
67. Key Management
68. Public-key authority
69. Public-key certificates
70. Public Key Distribution of Secret Keys
Each topic is complete with diagrams, equations and other forms of graphical representations for better learning and quick understanding.
Network Management & Security is part of Cloud computing security, computer science engineering, networking, software and communications, software engineering programs education courses and information technology degree programs at various universities.
Get free Primogems, Mora, Experience, and more with these November 2024 Genshin Impact codes, 5.1 livestream codes, and find out how to redeem active codes.
If you are bored with playing the vanilla version of Metaphor ReFantazio, you can check out these five mods.
Struggling with your submissions for Roblox's The Haunt event in 2024? Check out our guide on using Dress to Impress to create your captures!
Our walkthrough for Dragon Age: The Veilguard with some handy tips and tricks, with guides for puzzles, bosses, companions, equipment, romance, and more!
Which faction should you pick in Dragon Age: The Veilguard?
Looking for some bonus resources in Sea of Conquest: Pirate War? We’ve got you covered with these codes for the latest seafaring freebies.
On our website, you can easily download the latest version of Network Management & Security! No registration and SMS required!